Your cart is currently empty!
Why does ‘Smishing’ feel like a personal attack on each of us?
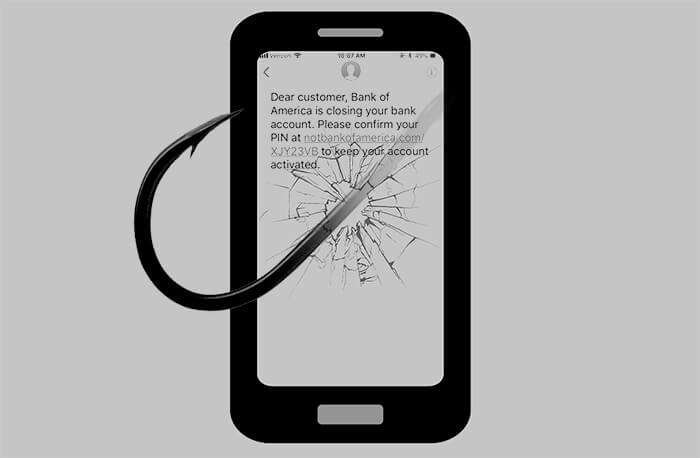
‘Smishing’ is the latest cyber bait that hackers are using to tempt us into taking a nibble. It’s essentially an old cyberscam gift wrapped inside a new box but why does this new attack vector in the war on cybersecurity feel more personal than before?
Most of us have heard of phishing attacks by now. When they work, they usually involve a link sent via email to an unsuspecting user. The user is fooled into thinking the email is a legitimate correspondence from a company or colleague that they need to look into. Within that message, a link promising to take them directly to the issue or prize or warning at hand is presented. If they’re lucky, the link doesn’t try to install malware directly onto their computer but instead, presents them with a login to an online store that they most likely have frequented before such as Amazon.com or Apple.com. This login page looks legitimate but has actually been setup for the sole purpose of collecting usernames, emails and passwords. Of course these phony login pages can also come in the form of online banking, social media alerts and other tech companies. According to Vade, in 2021 the most impersonated brand in phishing attacks was Facebook representing 14% of all attacks with companies like Microsoft, Chase and PayPal not too far behind the social media giant’s lead.
But phishing attacks are so 2021. As we approach the middle of 2022, we find ourselves staring into the face of the latest cyberattack called Smishing. You may have heard of whale phishing, spear phishing, vishing and even pharming, but smishing gets its “sm” prefix from the SMS in text messages because that is exactly how it is delivered. Like emails, some of these smishing texts are annoying spam, relatively harmless but how can you tell the harmless ones from the truly malevolent ones? You can’t, at least not without clicking on it which you should NEVER do. So what should you do?
In March of 2022, the average American received 42 spam text messages. Ever since the pandemic, smartphone users have stayed home and embraced their personal devices even more than before and cybercriminals have taken note. We’ve all experienced voice calls or voicemails that turn out to be spam. Due to the government entanglements between the FCC, FTC and large wireless carriers, robocalls have plagued the American public since the Trump administration tried to take them on in 2019. They are difficult to permanently stop, albeit easier to ignore, than most text messages. This is because emails and phone numbers are easy for cybercriminals and shady marketing firms to spoof. We have spam filters in our email clients that can catch hundreds of bogus emails each day and can also make our phones go directly to voicemail for any numbers that we do not recognize but what about text messages?
Over the past decade, text messages have become a bastion of private conversations between consenting smartphone users. We experience all of the emojis there; from rage to joy to sexting. We might even text things to people that we would never say in normal conversation. While email can be as impersonal as the old fashioned white pages in the phonebook for many, texting can be as intimate as relationship with our own therapist. This is why smishing can feel like a violation of our privacy and security. Cybercriminals are spoofing friends, family and even our ourselves by using cell numbers found in our area code or contact list. And this doesn’t even touch on the cybersecurity concerns.
Crypto scams are on the rise and fake prize offerings, warranty updates and credit ratings have all become part of our daily texting experience. You can try to delete the conversation but the same text can pop up again from another number which is as easy to spoof as the scammy text message itself. Even if there is no link within the text, you can be sure that cybercriminals are playing the long game by trying to bait us into a text conversation that will eventually lead to you revealing some personal information or clicking on a link promising to take you to somewhere special.
So can we do anything about this? If you do not recognize the name or number of the incoming text, DO NOT RESPOND. As much as you might have the desire to know “Who Dis?”, you should ignore or delete any unknown messages. If you respond, they know they have a live one on their smishing line and will only increase the frequency of messages and probably put you on a list with other active responders to target more in the future. You can also take your security and privacy one step further by blocking them entirely. If the text originated as an email, you can block that email so that you ever see it in your mailbox or text message again. For iPhone users, you might have to actually create that email as a contact before you can block it entirely.
Unfortunately, there is little more we can do to stop incoming text spams and scams beyond those simple tips. Until SMS filtering and security tools evolve more or the wireless carriers, tech companies and federal government all get on the same page in the fight against smishing, we will continue to see a rise in this personal digital violation.

Scott Schober
CEO | Author | Speaker at Berkeley Varitronics Systems
Scott Schober presents at cybersecurity and wireless security conferences for banking, insurance, transportation, construction, telecommunications and law enforcement industries. He has overseen the development of dozens of wireless test, security, safety and cybersecurity products used to enforce a “no cell phone policy” in correctional, law enforcement, and secured government facilities. Scott regularly appears on network news programs including Fox, Bloomberg, Good Morning America, CNN, MSNBC, NPR and many more. He is the author of 'Senior Cyber', 'Cybersecurity is Everybody's Business' and 'Hacked Again', the “original hacker’s dictionary for small business owners” - Forbes Magazine.
Our Newsletter
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Aliquam mattis ligula vitae leo scelerisque, sit amet feugiat ex venenatis.
"*" indicates required fields
Latest Posts
Our Best Sellers
How can we help?
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nunc dictum aliquet justo sit amet consectetur. In tempor lobortis ante vitae ornare. Praesent feugiat magna at tempor consequat. Aenean in iaculis libero, aliquam imperdiet mi.









Leave a Reply