Your cart is currently empty!
Largest security threat to the U.S. is US

As a cybersecurity expert and CEO of a company providing wireless threat detection solutions to many government agencies including the Department of Defense and White House, I’ve seen it all. We try to design products that are dead simple to operate while also offering multiple layers of security to government, military and law enforcement agencies and that includes many SCIFs (Sensitive Compartmented Information Facility), but humans are usually the weakest link of any security system. I’ve seen security systems hacked, bypassed and incorrectly operated or installed but this week we all learned that the largest security threat to the U.S. is us.
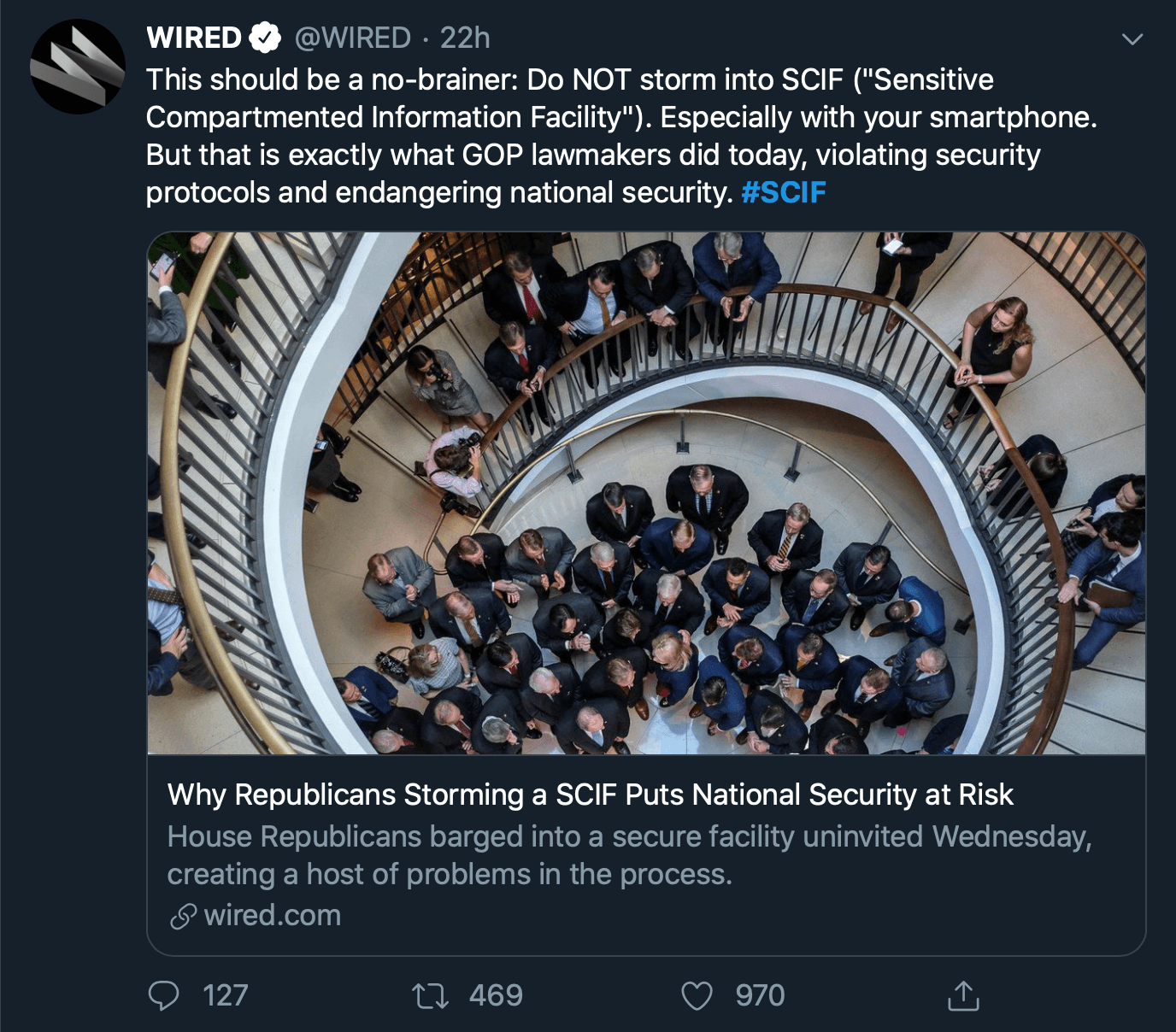
Representative Matt Gaetz (R-Florida) led some 30 other representatives into an active SCIF area where Adam Schiff (D-California) was conducting secret impeachment depositions. I won’t speculate into the motivations behind the disruption in order to avoid political bias, but we can discuss security protocols and why they are so vital. Many representatives that entered the SCIF area were carrying smart phones on their person and yet they were not searched nor stopped at the door. You may recall stories involving President Obama’s White House situation room during the raid on Osama Bin Laden’s compound in Pakistan. This very same room was originally set up for President Kennedy for his failed invasion of Cuba back in 1961 and is like most other SCIFs. SCIFs are simply rooms or areas designed to keep information from leaking into or out of by means other than person to person. This requires thick walls, locking doors and sometimes even armed guards. Since SCIFs are more about keeping information private than keeping invaders out of, they can even be set up as impromptu tents. So long as the flow of information is not intercepted, blocked or recorded, the SCIF is doing its job.
The reason we’ve only heard stories but have seen no pictures or video (except official White house releases) from that room is because all electronic recording devices are strictly forbidden from entering any SCIFs. These rooms ensure that communication between important officials is private and cannot get leaked.
With so many miniaturized electronic devices available today, it’s a real challenge to detect, locate and confiscate all of them. In my company’s dealings with various government agencies, I have overseen the development of many security systems that hone in on minuscule elements found in today’s smart phones as well as tablets, laptops, wireless earbuds, etc. This might sound as easy as walking someone through a metal detector but I can assure you that modern phones are made mostly of plastic. There is also a plethora of licensed and unlicensed RF (Radio Frequency) energy moving throughout our homes, business and public spaces so specifically detecting cellular frequencies in order to avoid false triggers is no trivial matter either. My company has developed a suite of products and we have sold thousands of these units to agencies ranging from corrections to every branch of the military and all the way up to the White House. Unfortunately, all security devices are ineffective when security protocols are ignored which is exactly what happened the other day when republicans stormed a SCIF the other day.
No one is accusing these republicans of leaking or spying but these security protocols are in place for a reason. Suppose one of the contraband phones that breached the SCIF contained malware. It’s not very difficult to imagine, considering just how much malware has been discovered on smartphones and that doesn’t even include all of the malware that we haven’t found on them! Malware, trojans and ransomware can all be used to activate recording and transmission of data on any device remotely from anywhere in the world. So a seemingly benign and temporary breach of security protocol can be likened to inviting Russia, China or North Korean spies into areas with sensitive information about the U.S.
We know that these SCIFs utilize security products and we also know that security personnel are posted outside and inside of all these SCIFs as well. Hopefully, we can all get on the same page as a country and put our partisan politics aside to (at the very least) activate and enforce these security protocols that all U.S. taxpayers have already paid for. Without the assurance of basic security and privacy, the only thing we can be sure of is that we are our own biggest national security threat.

Scott Schober
CEO | Author | Speaker at Berkeley Varitronics Systems
Scott Schober presents at cybersecurity and wireless security conferences for banking, insurance, transportation, construction, telecommunications and law enforcement industries. He has overseen the development of dozens of wireless test, security, safety and cybersecurity products used to enforce a “no cell phone policy” in correctional, law enforcement, and secured government facilities. Scott regularly appears on network news programs including Fox, Bloomberg, Good Morning America, CNN, MSNBC, NPR and many more. He is the author of 'Senior Cyber', 'Cybersecurity is Everybody's Business' and 'Hacked Again', the “original hacker’s dictionary for small business owners” - Forbes Magazine.
Our Newsletter
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Aliquam mattis ligula vitae leo scelerisque, sit amet feugiat ex venenatis.
"*" indicates required fields
Latest Posts
Our Best Sellers
How can we help?
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nunc dictum aliquet justo sit amet consectetur. In tempor lobortis ante vitae ornare. Praesent feugiat magna at tempor consequat. Aenean in iaculis libero, aliquam imperdiet mi.









Leave a Reply