Your cart is currently empty!
This is why nobody is allowed a cell phone in classified debriefings
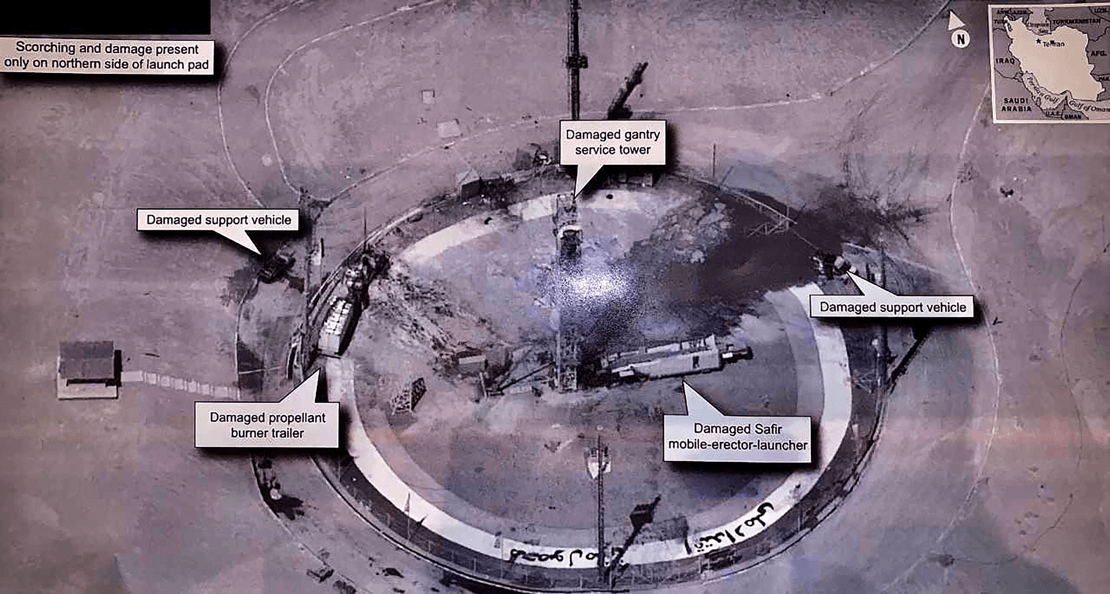
Three years ago, former President Trump tweeted this image along with a denial of the U.S.’ involvement with a launch accident involving Iran’s Safir SLV rocket. Now, this image has been officially declassified so why are Pentagon and intelligence officials so disturbed?
Trump’s controversial handling of classified documents is nothing new. When his Mar-a-Lago home was raided back in August, piles of classified and declassified papers were discovered. Trump offered several explanations (some of them contradictory) for the appearance of these documents in his personal office and home. That investigation is ongoing but this tweet in question is over 3 years old so why is the intelligence community speaking out now? While political motivations are likely behind many of these concerns, there are also legitimate concerns over the handling of sensitive information by anyone, even the most powerful person in government.
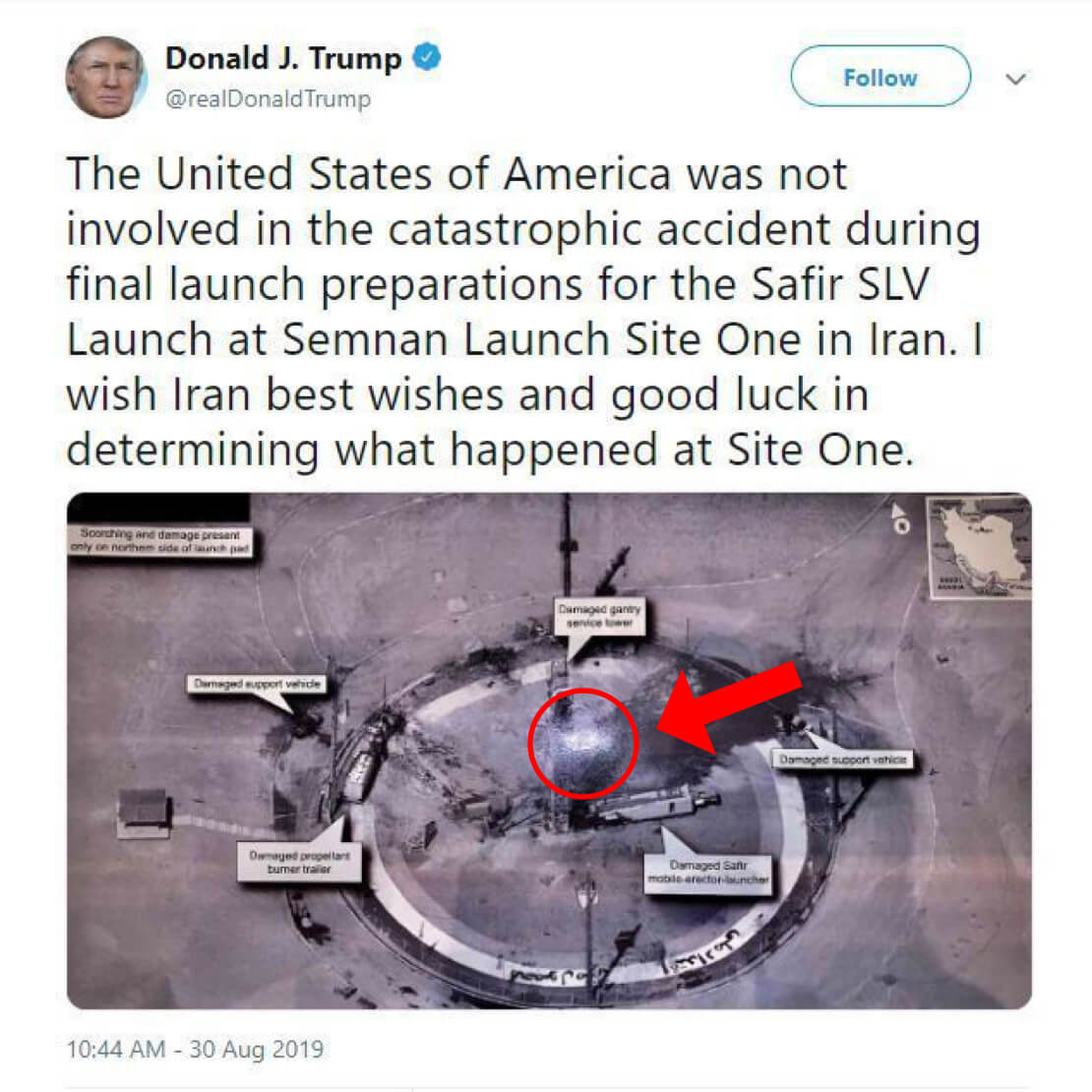
Looking at Trump’s own tweet (see image below), it becomes clear that he (or someone using his phone) simply snapped a pic during a classified debriefing. The glare in the center of the photo (I’ve added red circle and arrow) and shadow are a dead giveaway that this image was either re-photographed or projected against a wall as indicated by the glare from an overhead light or reflected light from a projector. Once the image ended up in the President’s phone’s camera roll, it was a simple matter of inserting it into a tweet for the world to see.
We’ve had years of media speculation as to why Trump flouted security protocol the way he did so I don’t want to revisit those arguments, but as a cybersecurity expert and CEO of a wireless security company that deals with Dept. of Defense agencies and customers everyday, I want to touch upon a few basic security tenets.
According to Business Insider, Trump asked to keep a copy of this photo he first saw during a daily intelligence briefing. An hour later, the photo and his tweet went out to his 60 million Twitter followers. Trump claimed to do nothing wrong at the time but I’m more interested in how we even got to this point.
Classified data and briefings are generally communicated through SCIFs (Sensitive Compartmentalized Information Facility) within secure facilities. SCIFs (learn all about SCIFs here) are generally small enclosures sealed off and air-gapped from all electronic communications. All wireless communications inside and around the SCIF are monitored for any transmissions and the entire SCIF is swept for bugs and any rogue PEDs (Personal Electronic Devices) prior to any debriefing. Finally, everyone entering the SCIF is searched and asked to relinquish any PEDs on their person. This includes the President of the United States of America.
These layers of security and protocol have been followed by the intelligence community for decades for good reason. Bringing an unsecured consumer smartphone into a classified meeting puts everyone in danger. Wi-Fi, Bluetooth, BLE, 5G and any wireless communication standard – none are truly secure. We know this because we have manufactured and sold tens of thousands of wireless security tools to law enforcement, government agencies and private companies over the past decade. Through malware, hackers have repeatedly demonstrated the ability to hijack phones and steal data without their owner’s knowledge. Once they acquire that data, hackers have all the power by selling state secrets to enemies or by making demands through ransomware already installed on the insecure devices.
Security portals stop all personal electronic devices (powered on or off) at the door and handheld receivers sweep secure facilities for hidden bugs and nearby active rogue devices but these tools are only as good as their operators and security protocols in place. All security personnel must follow best practices in detection, location and seizure of all personal electronic devices in order to avoid leaks, hacks and theft of classified information. These rules apply to everyone in an organization, even the President.

Scott Schober
CEO | Author | Speaker at Berkeley Varitronics Systems
Scott Schober presents at cybersecurity and wireless security conferences for banking, insurance, transportation, construction, telecommunications and law enforcement industries. He has overseen the development of dozens of wireless test, security, safety and cybersecurity products used to enforce a “no cell phone policy” in correctional, law enforcement, and secured government facilities. Scott regularly appears on network news programs including Fox, Bloomberg, Good Morning America, CNN, MSNBC, NPR and many more. He is the author of 'Senior Cyber', 'Cybersecurity is Everybody's Business' and 'Hacked Again', the “original hacker’s dictionary for small business owners” - Forbes Magazine.
Our Newsletter
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Aliquam mattis ligula vitae leo scelerisque, sit amet feugiat ex venenatis.
"*" indicates required fields
Latest Posts
Our Best Sellers
How can we help?
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nunc dictum aliquet justo sit amet consectetur. In tempor lobortis ante vitae ornare. Praesent feugiat magna at tempor consequat. Aenean in iaculis libero, aliquam imperdiet mi.









Leave a Reply